Hybrid Firewall Architecture for SMBs: Connecting LAN and Cloud Seamlessly
The SMB Network Has Become Hybrid
Many SMBs today operate hybrid networks not by strategic choice, but by necessity.
File servers still live on local LANs. Core business applications run on SaaS platforms. Some workloads have quietly moved to cloud environments like AWS or Azure. Employees switch daily between office, home, and remote locations.
The business impact is subtle but real:
Security rules drift, visibility breaks across environments, and every network change costs more operational effort than it should.
Traditional LAN-centric firewall models were never designed to govern traffic consistently across LAN, cloud, remote users, and branch locations at the same time. As a result, SMB IT teams spend more time compensating for architectural gaps than supporting business growth.
This blog explains how a practical hybrid firewall architecture helps SMBs regain consistency and operational control across LAN, cloud, branches, and remote access without introducing enterprise-level complexity.
What Hybrid Firewall Architecture Really Means
A hybrid firewall architecture is not about deploying multiple firewalls in different places.
It is about enforcing a single security and routing logic across multiple environments LAN, cloud, branches, and remote access regardless of where the firewall runs.
Hybrid firewalls have a total of 3 layers, each of them serve a clear purpose.
The first layer is called the Policy Plane. It unifies objects and identities across users, roles, network segments, and subnets, allowing a single set of rules to apply across multiple form factors. This ensures consistent policy enforcement from the LAN to VPN connections, cloud workloads, and branch locations.
The second layer is the Control Plane. The Control Plane orchestrates the full network topology, delivering unified routing and segmentation.. It manages internal segments, connects LAN to cloud, links branches to headquarters, and routes remote users while keeping cloud workloads fully integrated within the internal segmentation for consistent visibility and control. Importantly, this layer allows cloud workloads to remain fully part of the internal segmentation instead of being isolated.
And the last layer, the Data Plane, provides deployment flexibility, allowing the firewall to run on a box-on-prem, VPN gateway, or hybrid cloud firewall. Despite the differences in form, the firewall maintains a unified processing logic and a consistent understanding of segments and policies, avoiding a patchwork of multi-vendor solutions.
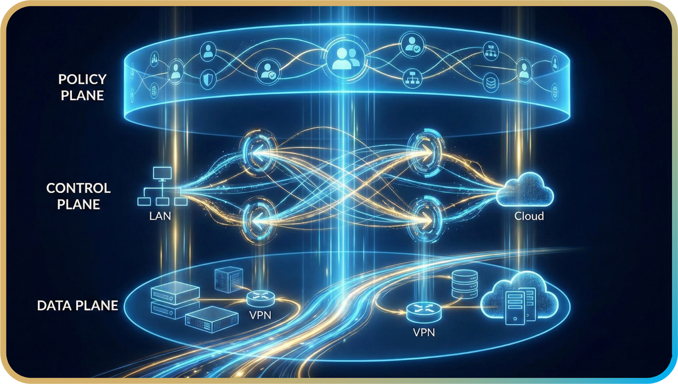
Unify rules, orchestrate topology, and execute consistently anywhere through a structured, three-plane architecture.
Technical Problems Hybrid Firewall Solves
When network topology evolves faster than the firewall policy model, technical problems are inevitable.
Most SMB networks now span three distinct environments: LAN, VPN, and cloud. Each environment behaves differently in how traffic is identified, routed, and logged. Over time, these differences create small policy inconsistencies that accumulate into structural operational issues.
Stop Rebuilding Rules: How Unified Policies Secure the Entire Hybrid Network
SMB hybrid network architecture often runs three parallel worlds of access control. LAN rules follow one logic, VPN rules follow another, and cloud environments introduce their own set of policies. All of this combined makes the security model become fractured.
This fragmentation leads to practical inconsistencies: users on an office LAN might be blocked from a resource, yet the same identity is permitted when connecting remotely. Moreover, as SaaS traffic traverses the Internet and VPC workloads move through private tunnels, it creates split visibility and complex routing. This makes it extremely hard for traditional firewalls to monitor and maintain policy consistency.
Applying a unified firewall policy model solves this by unifying objects and zone-based rules across all environments. Under this approach, policies are written once and enforced consistently across LAN, VPN, and cloud paths. Applications and segments map directly to each other without deviations, ensuring the security intent stays intact regardless of where traffic originates.
The result is a much cleaner operational model where rewriting rules for every infrastructure shift is no longer needed. Because policies remain synchronized, IT teams can finally stop "firefighting" security inconsistencies and focus on initiatives that directly support business growth.
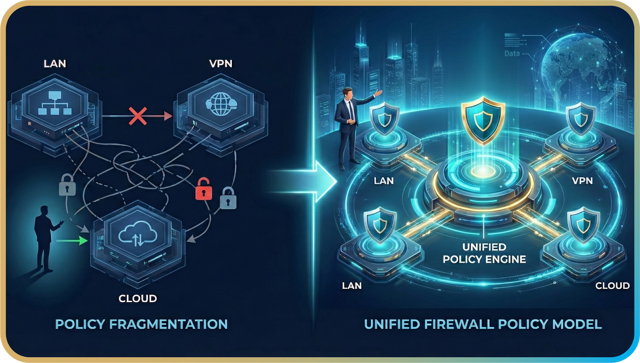
Unifying fragmented policies across LAN, VPN, and Cloud into a single, consistent security model.
Visibility Gaps Across LAN and Cloud
Logs are collected extensively from LAN, VPN, and Cloud workloads including VPC and SaaS by SMBs everyday, yet the data remains fragmented. The core issue is context loss. In practice, this means IT teams may see a user authentication log, a VPN tunnel log, and a cloud access log, but without a clear way to correlate them into a single end-to-end session. When a single session traverses multiple environments, IT sees only disconnected log entries, failing to reconstruct the complete full path flow. This fragmentation creates critical “blind spots”, severely hindering the detection of anomalies and security tracing efforts.
A hybrid firewall provides flow-based logging across the entire SMBs network, capturing end-to-end traffic from user or device to cloud destination. Each session is mapped clearly: user/device → segment → interface/tunnel → cloud destination. Coupled with firewall routing visibility, this approach visualizes traffic paths following SMB hybrid topology security logic.
With unified routing and segmentation, IT teams can precisely understand the path of applications through every segment of the network. Anomalies are detected more quickly, troubleshooting cycles are shortened, and operational reliability improves.
Scaling Branch or Cloud Without Rebuilding Architecture
The fundamental challenge in scaling traditional security is that the old rigid model makes expansion inherently difficult. When a new branch opens, firewall rules are required to be rewritten, and moving an app from LAN to cloud often results in the firewall being treated as an untrusted internet segment. This inefficiency is not a simple operational hurdle; it's an architectural bottleneck where the existing topology actively prevents simple scaling, forcing SMBs to rebuild their security model with every expansion.
This flexible SMB firewall solution addresses this via a Hub-and-Spoke model where the cloud VPC is viewed as another segment belonging to the unified topology. Crucially, it replaces device configurations with Template-based branch policies. This shift from specific rules to templates means that security models are built once and applied consistently. Having a unified firewall policy will eliminate the need to tear down and rebuild security logic whenever a new site is opened.
SMBs can scale from one site to five without manually rewriting the entire rule base, achieving policy consistency. Cloud workloads are an integrated segment within the firewall’s unified topology. This future-proofs hybrid firewall architecture, allowing IT to focus on business enablement rather than constant security work.

Expanding branches and cloud segments without rewriting rules or rebuilding architecture.
Practical SMB Scenarios: Real-World Applications
Scenario 1: Head Quarter with Small Branches
In this architecture, the HQ firewall serves as the central hub. Small branch routers or CPE simply establish a persistent tunnel back to this hub,acting as a simplified branch connectivity firewall. Crucially, the firewall logic segments this branch traffic exactly as if it were a local LAN zone. This allows the administrator to apply a single Zone Policy that governs both the HQ and the branch simultaneously. The branch effectively becomes a natural extension of your main office LAN. You gain full-path logging and security visibility without the cost of deploying complex security hardware at every micro-site.
Scenario 2: SMBs needing a firewall for small business cloud and SaaS
The firewall takes control of the routing logic between Internal networks, internet and cloud environments. It defines VPN tunnels or peering to the cloud specifically as a “Cloud Segment” within the topology. By optionally using a virtual firewall in a cloud environment with the same object and rule logic, the system distinguishes trusted cloud infrastructure traffic from generic web browsing
Their cloud servers are no longer treated like “Internet random destinations”. This eliminates routing confusion and ensures that security policies for traffic flowing between your LAN and your cloud instances are clear.
Scenario 3: Hybrid Work (Users move between office & remote)
Whether a user is on-site or remote, the firewall identifies traffic based on User Identity, Role, and Segment. Routing and security decisions are made using this user context rather than static IP ranges. This unifies the rule base, removing the need for duplicate policies for VPN vs LAN. With this LAN-to-cloud connectivity, the employees can get a consistent experience, and the company can get consistent enforcement

Enforcing security based on User Identity, not static IPs, to bridge the gap between on-site and remote work.
Scenario 4: Building an SD-WAN Ready Foundation
Deploying a Hybrid Firewall architecture establishes a standardized model for segmentation, zones, and objects from day one. This means the network foundation is prepared. Implementing SD-WAN later becomes a simple process of enabling features like: uplink selection, traffic steering and health-check logic. The fear of “breaking the architecture” no longer exists. You do not need to rip and replace your security model to get faster internet or better redundancy later. The firewall serves as a scalable foundation that grows with your business complexity.
Beyond Legacy Firewalls: How AIDATACY Solves the Encryption Gap Without Adding Complexity
At AIDATACY, our hybrid firewall is designed to understand network topology and traffic flows, even when the traffic itself is encrypted.
We move beyond the heavy complexity of traditional enterprise solutions by focusing on metadata-based routing and encrypted flow visibility to maintain control across hybrid environments. Instead of relying on intrusive deep packet inspection, our architecture leverages flow behavior and segmentation logic to reconstruct the full path from user identity to destination.
Our approach is built for the reality of modern business: our hybrid firewall connects LAN, cloud, branch, and remote teams through a single, unified logic. While traditional Fortinet or Meraki-like setups often require resource-heavy SSL decryption or complex rule sets for every location, AIDATACY provides deep visibility without decryption. This matters operationally because it eliminates the performance bottlenecks and certificate management headaches that typically overwhelm small IT teams.
By using a Segment-based Policy model, we ensure that security remains consistent no matter where your data lives. Designed as a lightweight solution for SMBs, our architecture allows for simple branch extension and efficient management without the need for a dedicated Security Operations Center.
“We don’t rebuild enterprise mesh architectures.
We give SMBs a unified, practical firewall foundation that keeps LAN, cloud, and remote users consistent and easy to operate.”
Don't just rely on theory. Let AIDATACY engineers analyze your current infrastructure and simulate a hybrid firewall solution tailored to your reality. Contact us here





